This article contains a list of the available decrypter tools to recover your infected files from known Ransomware viruses for free. A Ransomware virus is a type of malware that lock down user files with strong data encryption and after file encryption (infection) demands a ransom payment from the user in order to unlock the encrypted files.
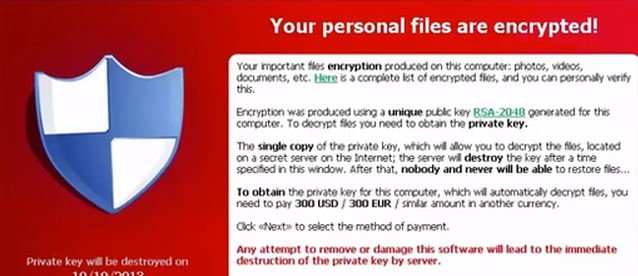
In most cases Ransomware, encrypts user files and changes the file extension to something else and from this modification you can easily find out from which type of Ransomware you are infected. For that case, I wrote this article which contains a list of several known ransomware variants, the extension that added after the ransomware infection and the available decryptor tools and methods to unlock the infected files.
If you become a ransomware victim, perform the following steps:
STEP 1. Remove the infected computer from the network.
STEP 2. Identify from which ransomware variant you are infected with, by following one of the following methods:
Method-1. Find out (see) if the original filenames and extensions of your files are changed to something different (e.g. from “Document1.docx” to “Document1.docx.micro“) . To accomplish this task you may need to enable the hidden files View and the file extensions View from: Folder Options -> View tab -> Show Hidden Files, folders & Un-Hide extensions for known file types.
Method-2. If you cannot identify the ransomware name/variant then navigate to ID Ransomware website and upload the Ransom Note and a Sample of an Encrypted file to identify the ransomware that has encrypted your data.
STEP 3. See the Ransomware list bellow, in order to find out from which ransomware virus are you infected with and then follow the link (at the ransomware name) to find out if there is available a decrypter tool or a decrypt method to unlock your files for free.
If a Ransomware Decrypter tool is not available yet, then:
1. Make backup copies of the affected data to another storage device, in a case of a future solution.
2. Remove the threat from the infected system.
3. Try to restore you system to a previous working restore point or restore your files by using the previous versions feature or even better the Shadow Explorer utility, if you are lucky and the ransomware hasn’t deleted the Shadow Volume (Restore Points) copies.
You should not pay the ransom, because you encourage the criminals to keep infecting systems and demanding money from victims.
List of Ransomware (Names, Extensions).
| Ransomware_Name | Filename_after_infection | Ransomware Extension |
| .777 | {Original Filename} | .777 |
| 7ev3n-HONE$T | {Changed Filename} | .R4A, .R5A |
| 8lock8 | {Original Filename} | .8lock8 |
| Al-Namrood | {Original Filename} | .unavailable OR .disappeared |
| Alfa or Alpha | {Original Filename} | .bin |
| Alma Locker | {Original Filename} | .5 random characters |
| Apocalypse (Libra) | {Original Filename} | .encrypted, .FuckYourData, .locked, .Encryptedfile, .SecureCrypted |
| ApocalypseVM | {Original Filename} | .encrypted, .locked |
| AutoIt | {Original Filename}@<mail server> | .<random_set_of_characters> |
| BadBlock | {Original Filename} | |
| Bandarchor | {Original Filename} | Fud@india.com |
| Bart | {Original Filename} | .bart.zip |
| BitCryptor | {Original Filename} | .clf |
| Bitman | {Original Filename} | .xxx, .ttt, .micro, .mp3 |
| Bitman V4 (TeslaCrypt V4) | {Original Filename} | {Original Extension} |
| BitStak | {Changed Filename} | .bitstak |
| Black Shades | {Original Filename} | .silent |
| Booyah | {Original Filename} | {Original Extension} |
| CERBER V1 | {10 random characters} | .cerber |
| CERBER V2 | {10 random characters} | .cerber2 |
| Chimera | {Original Filename} | .crypt |
| CoinVault | {Original Filename} | |
| Cryakl | {Original Filename} + {CRYPTENDBLACKDC} | |
| CryLocker or CryPy | {Changed Filename} | .cry |
| CrypBoss | {Original Filename} | .crypt, .R16M01D05 |
| Crypt888 or MirCop | Lock.{Original file name} | |
| CryptInfinite | {Original Filename} | .CRINF |
| CryptoDefense | {Original Filename} | |
| Cryptolocker | {Original Filename} | |
| Crypt0L0cker or TorrentLocker | {Original Filename} | .encrypted, .enc |
| Cryptorbit | {Original Filename} | |
| Cryptowall | {Original Filename} | |
| CryptXXX V1, V2, V3 | {Original Filename} | .crypt, .crypt1 |
| CryptXXX V4, V5 | {MD5 Hash} | .5 hexadecimal characters |
| Crysis | {Original Filename} | .id-email-address.xtbl, .id-email-address.xtbl.CrySiS |
| Democry (Legion | {Original Filename} | ._date-time_$address@domain$.777, ._date-time_$address@domain$.legion |
| DMALocker & DMALocker2 | {Original Filename} | |
| DXXD | {Original Filename} | .{Original Extension}DXXD |
| Fabiansomware | {Original Filename} | .encrypted |
| FenixLocker | {Original Filename} | .centrumfr@india.com |
| Globe | {Original Filename} | .purge, .globe, .okean |
| Globe2 | {Original Filename} | .raid10, .blt, .globe, .encrypted, .[mia.kokers@aol.com] |
| Gomasom | {Original Filename} + Email Address | .crypt |
| Harasom | {Original Filename} | .HTML |
| Jigsaw | {Original Filename} | .FUN, .KKK, .GWS, .BTC |
| HydraCrypt | {Original Filename} | .hydracrypt |
| KeyBTC | {Original Filename} | .keybtc@inbox_com |
| LECHIFFRE | {Original Filename} | .LeChiffre |
| Legion (Democry | {Original Filename} | ._date-time_$address@domain$.777, ._date-time_$address@domain$.legion |
| Libra (Apocalypse) | {Original Filename} | .encrypted, .FuckYourData, .locked, .Encryptedfile, .SecureCrypted |
| Lobzik | {Original Filename} | .fun, .gws, .btc, .AFD, .porno, .pornoransom, .epic, .encrypted, .J, .payransom, .paybtcs, .paymds, .paymrss, .paymrts, .paymst, .paymts, .payrms |
| LockLock | .locklock | |
| Locky & AutoLocky | In case of Locky: {Filename Changed} In case of Autolocky: {Original Filename} | .locky, .zzzzz |
| MirCop or Crypt888 | Lock. {Original file name} | |
| Nemucod | {Original Filename} | .crypted |
| NoobCrypt | ||
| Operation Global III (OG3) | {Original Filename} | .exe |
| OzozaLocker | {Original Filename} | .locked |
| PClock / {Original Filename} / – | {Original Filename} | |
| Petya | ||
| Philadelphia | {Changed Filename} (Encrypted) | .locked |
| Princess Locker | {Original Filename} | {Random Extension} |
| Radamant | {Original Filename} | .rdm or .rrk |
| Rakhni (and others…) | {Original Filename} | .locked, .kraken, .darkness, .nochance, .oshit, .oplata@qq_com, .relock@qq_com, .crypto, .helpdecrypt@ukr.net, .pizda@qq_com, .dyatel@qq_com, ._crypt .nalog@qq_com, .chifrator@qq_com, .gruzin@qq_com, .troyancoder@qq_com, .encrypted, .cry, .AES256, .enc, .coderksu@gmail_com_id371, .coderksu@gmail_com_id372, .coderksu@gmail_com_id374, .coderksu@gmail_com_id375, .coderksu@gmail_com_id376, .coderksu@gmail_com_id392, .coderksu@gmail_com_id357, .coderksu@gmail_com_id356, .coderksu@gmail_com_id358, .coderksu@gmail_com_id359, .coderksu@gmail_com_id360, .coderksu@gmail_com_id20, .crypt@india.com.random_characters, .+<hb15 |
| Rannoh | locked-{Original Filename} | .<four_random_letters>. |
| Rector | {Original Filename} | |
| Shade V1 & V2 | .xtbl, .ytbl, .breaking_bad, .heisenberg | |
| SZFLocker | {Original Filename} | .szf |
| SNSLocker | {Original Filename} | .RSNSLocked |
| Stampado | {Original Filename} | .locked |
| TeslaCrypt V1.0 | {Original Filename} | .ecc |
| TeslaCrypt V2.0 | {Original Filename} | .ezz, .exx, .xyz, .zzz,. aaa, .abc, .ccc, & .vvv |
| TeslaCrypt V3.0 (Bitman V3.0) | {Original Filename} | .xxx, .ttt, .micro, .mp3 |
| TeslaCrypt V4.0 (Bitman V4.0) | {Original Filename} | {Original Extension} |
| TorrentLocker or Crypt0L0cker | {Original Filename} | .encrypted, .enc |
| UmbreCrypt / {Original Filename} | {Original Filename} | .umbrecrypt |
| Wildfire | .wflx | |
| XORBAT | {Original Filename} | .crypted |
| XORIST & VANDEV | {Original Filename} | .xorist (OR random extension) |
| XRatTeam / TeamXRat | {Original Filename} | .xratteamLucked |
| Zepto | {Changed Filename} | .zepto |
List of free Decryptor Tools by Ransomware Name.
777
The 777 ransomware adds the extension “.777″ at the end of each infected file and creates the following ransom notes: read_this_file.txt
How to decrypt files encrypted by 777 virus.
To recover 777 encrypted files use one of the following decryptor tools:
1. Trend Micro Ransomware File Decryptor
2. Emsisoft Decrypter for 777
7ev3n-HONE$T
7ev3n-HONE$T encrypts your data and renames your files to sequential numbers using the .R5A extension. (e.g. 1.R5A, 2.R5A, 3.R5A, etc.)
How to decrypt files encrypted by 7ev3n-HONE$T.
Unfortunately at this time it’s not possible to recover files encrypted by the 7ev3n-HONE$T ransomware.
8lock8
The 8lock8 ransomware adds the extension “.8lock8″ at the end of each infected file and creates the following ransom notes: READ_IT.txt
How to decrypt files encrypted by .8lock8 virus.
To recover 8lock8 encrypted files follow the instructions from here.
Al-Namrood
The Al-Namrood adds the extension .unavailable or .disappeared at the end of each infected file.
How to decrypt files encrypted by Al-Namrood.
In order to decrypt Al-Namrood encrypted files use the Emsisoft Decrypter for Al-Namrood
Alfa or Alpha
The Alfa (also known as “Alpha”) ransomware adds the extension “.bin” at the end of each infected file and creates the following ransom notes: README HOW TO DECRYPT YOUR FILES.HTML and README HOW TO DECRYPT YOUR FILES.TXT
How to decrypt files encrypted by Alfa virus.
Unfortunately at this time it’s not possible to recover files encrypted by Alfa ransomware.
Alma Locker
The Alma Locker adds 5 random characters at the end of each infected file (e.g. “.b5er3“) and a unique 8 character victim ID.
How to decrypt files encrypted by Alma Locker.
In order to decrypt Alma Locker encrypted files use the Alma Ransomware Decrypter tool.
Apocalypse (Libra)
The Apocalypse ransomware (also known as “Libra”) encrypts user data and adds the following extensions to the end of filenames: .encrypted, .FuckYourData, .locked, .Encryptedfile, or .SecureCrypted. Also Apocalypse creates the following ransom notes at every infected directory: How_To_Decrypt.txt, *.Where_my_files.txt, *.How_to_Recover_Data.txt or *.Contact_Here_To_Recover_Your_Files.txt.
How to decrypt files encrypted by Apocalypse / Libra.
In order to recover files encrypted by Apocalypse, you can use one of the following decryptor tools:
- AVG’s Apocalypse Decryption Tool
- Emsisoft Decrypter for Apocalypse
- Kaspersky RakhniDecryptor tool
ApocalypseVM
The ApocalypseVM ransomare during encryption adds the following extension to the end of filenames: .encrypted or .locked and creates the following ransom notes at every infected directory: *.How_To_Decrypt.txt, *.README.txt, *.How_to_Decrypt_Your_Files.txt or *.How_To_Get_Back.txt
How to decrypt files encrypted by ApocalypseVM.
In order to recover files encrypted by ApocalypseVM, you can use this tool: Emsisoft Decrypter for ApocalypseVM
AutoIt
Trojan-Ransom.Win32.AutoIt encrypts your files and during infection the file extensions are changed according to this template:
{Original Filename}@<mail server>_.<random_set_of_characters>.
How to decrypt files encrypted by AutoIt.
To recover AutoIt encrypted files use this tool: Kaspersky RannohDecryptor
BadBlock
The BadLock malware encrypts files but doesn’t change their filename. After infection creates the ransom notes Help Decrypt.html file on every infected directory.
How to decrypt files encrypted by BadLock.
In order to recover files encrypted by BadLock, you can use one of the following decryptor tools:
- AVG’s BadLock Decryption Tool
- Emsisoft Decrypter for BadBlock
- Trend Micro Ransomware File Decryptor
Bandarchor
The Bandarchor (also known as “Fud@india.com”) ransomware encrypts and renames files as “[filename].id-[ID]_fud@india.com”
How to decrypt files encrypted by Bandarchor Ransomware.
Unfortunately at this time it’s not possible to recover files encrypted by Bandarchor.
Bart
Bart ransomware adds the following extension to the end of filenames .bart.zip. Also creates the files recover.bmp & recover.txt to the desktop.
How to decrypt files encrypted by Bart.
In order to recover files encrypted by Bart, you can use this tool: AVG’s Bart Decryption Tool.
BitCryptor
The BitCryptor ransomware appends the extension .clf .
How to decrypt files encrypted by BitCryptor
To recover BitCryptor encrypted files use the following decryptor tool: Kaspersky CoinVault Decryptor tool
BitStak
BitStak changes the original filenames and adds the following extension to the end of filenames .bitstak
How to decrypt files encrypted by BitStak.
In order to recover files encrypted by BitStak ransomware, you can use this tool: BitStakDecrypter
Black Shades
The Black Shades ransomware adds the extension “.silent” at the end of each infected file and creates the following ransom notes: “YourID.txt” and “Ваш идентификатор“
How to decrypt files encrypted by Black Shades.
Unfortunately at this time it’s not possible to recover files encrypted by Black Shades ransomware.
Booyah
The Booyah malware encrypts files but doesn’t change their filename or extension. After infection creates the ransom notes WHATHAPPENDTOYOURFILES.TXT and the CRIPTOSO.KEY file on every infected directory
How to decrypt files encrypted by Booyah.
Unfortunately at this time it’s not possible to recover files encrypted by Booyah ransomware
CERBER V1
CERBER V1 malware changes the original filename with ten (10) random characters and adds the extension .cerber at the end of the filename of each infected file.
How to decrypt files encrypted by Cerber V1
In order to recover CERBER V1 encrypted files use Trend Micro Ransomware File Decryptor
CERBER V2
CERBER V2 malware changes the original filename with ten (10) random characters and adds the extension .cerber2 at the end of the filename of each infected file.
How to decrypt files encrypted by Cerber V2
Unfortunately at this time it’s not possible to recover the files encrypted by the Cerber2 ransomware. *
* Note: In the past, Check Point Software has released a free Cerber ransomware decryption tool to restore Cerber v1 & V2 encrypted files, but the service is no longer available.
Chimera
The Chimera ransomware adds the following extension at the end of each infected file: .crypt
How to decrypt files encrypted by Chimera
To recover Chimera encrypted files use one of the following decryptor tools:
- Kaspersky RakhniDecryptor tool
- Trend Micro Ransomware File Decryptor.
CoinVault
The CoinVault ransomware after encrypting your files displays a ransom note on your screen demanding for a ransom in order to decrypt your files.
How to decrypt files encrypted by CoinVault
To recover CoinVault encrypted files use the following decryptor tool: Kaspersky CoinVault Decryptor tool
Cryakl
Trojan-Ransom.Win32.Cryakl encrypts your files and after infection, adds the tag {CRYPTENDBLACKDC} at the end of file names.
How to decrypt files encrypted by Cryakl
To recover Cryakl encrypted files use this tool: Kaspersky RannohDecryptor.
CryLocker or CryPy
The CryLocker ransomware changes the original filename and adds the following extension at the end of each infected file: .cry. After infection creates ransom notes on the desktop “README_FOR_DECRYPT.txt“, instructing the user to contact the criminals at m4n14k@sigaint.org or blackone@sigaint.org.
How to decrypt files encrypted by CryLocker
Unfortunately at this time it’s not possible to recover CryLocker encrypted files.
CrypBoss
The CrypBoss ransomware renames the files by adding the following extensions: .crypt, .R16M01D05 and creates the ransom notes HELP_DECRYPT.jpg or HELP_DECRYPT.txt instructing the user to contact a @dr.com email address.
How to decrypt files encrypted by CrypBoss
To recover CrypBoss encrypted files use the following decryptor tool: Emsisoft Decrypter for CrypBoss
Crypt888 or MirCop
Crypt888 (or MirCop) adds the work Lock. at the beginning of each filename.
How to decrypt files encrypted by MirCop/Crypt888.
In order to recover files encrypted by Crypt888/MirCop, you can use one of the following tools:
- AVG Crypt888 Decryptor Tool.
- Trend Micro Ransomware File Decryptor
CryptInfinite
CryptInfinite malware adds the extension .CRINF at the end of each encrypted file and creates a file with ransom notes ReadDecryptFilesHere.txt in every infected directory.
How to decrypt files encrypted by CryptInfinite
To recover the CryptInfinite encrypted files use this tool: Emsisoft Decrypter for CryptInfinite
CryptoDefense
The CryptoDefense malware locks user files and create the following ransom notes at every infected directory: HOW_DECRYPT.txt, HOW_DECRYPT.html and HOW_DECRYPT.url
How to decrypt files encrypted by CryptoDefense
If your PC is infected with Cryptodefence, then use Emsisoft’s Cryptodefence Decrypter tool to unlock your files.
Cryptolocker
CryptoLocker Ransomware does not exist anymore and hasn’t since June 2014.
How to decrypt files encrypted by Cryptolocker.
FireEye & Fox-IT have released a service that retrieves the decryption key for users that were infected by the CryptoLocker Ransomware. The service is called ‘DecryptCryptoLocker’ but doesn’t exist anymore.
Crypt0l0cker or TorrentLocker
TorrentLocker (otherwise known as “Crypt0L0cker”) malware adds the following extensions to the end of each encrypted file: .encrypted or .enc and it will create a ransom note named “DECRYPT_INSTRUCTIONS.html” on your desktop.
How to decrypt files encrypted by TorrentLocker / Crypt0l0cker
Unfortunately at this time it’s not possible to recover the files encrypted by the TorrentLocker (Crypt0l0cker) ransomware.
Cryptorbit
The Cryptorbit malware locks user files and create the following ransom notes at every infected directory: HowDecrypt.txt, HowDecrypt.gif
How to decrypt files encrypted by Cryptorbit.
If your PC is infected with Cryptodefence, then use the Anti-CryptorBitV2 decryptor utility to recover Cryptorbit locked files ( JPG, PST, MP3, PDF, .DOC, .XLS, .XLSX, .PPTX, .and DOCX). (Source: How to fix files encrypted by CryptorBit using DecrypterFixer’s Tools)
Cryptowall
The Cryptowall malware locks user files and create the following ransom notes at every infected directory:
- Cryptowall & CryptoWall 2.0 (DECRYPT_INSTRUCTIONS.TXT, DECRYPT_INSTRUCTIONS.HTML)
- CryptoWall 3.0 (HELP_DECRYPT.HTML, HELP_DECRYPT.PNG, HELP_DECRYPT.TXT, and HELP_DECRYPT.URL)
- CryptoWall 4.0 (HELP_YOUR_FILES.PNG, HELP_YOUR_FILES.HTML, HELP_YOUR_FILES.TXT)
How to decrypt files encrypted by Cryptowall.
Unfortunately at this time there is no way to retrieve the private key or a decrypt tool that can be used to decrypt Cryptowall files without paying the ransom.
CryptXXX V1, V2, V3
CryptXXX V1 & CryptXXX V2, adds the following extensions to the end of filenames: .crypt, .crypt1
CryptXXX v3 adds the adds the following extension to the end of filenames: .cryptz or 5 hexadecimal characters.
How to decrypt files encrypted by CryptXXX V1, V2, V3
If your PC is infected with CryptXXX V1 or CryptXXX V2 then use one of the following tools to recover your files:
- Kaspersky RannohDecryptor
- Trend Micro Ransomware File Decryptor
CryptXXX V3 encoded files, can partially recovered with Trend Micro Ransomware File Decryptor tool.
CryptXXX V4, V5
CryptXXX V4 & CryptXXX V5, change the original filename (MD5 Hash) and adds 5 hexadecimal characters at the end of filenames.
How to decrypt files encrypted by CryptXXX V4, V5
To recover the files encrypted by CryptXXX V4, V5 malware use Trend Micro Ransomware File Decryptor tool.
Crysis
Crysis ransomare adds one of the following extensions to the end of each encrypted file: .id-email-address.xtbl, .id-email-address.xtbl.CrySiS
How to decrypt files encrypted by Crysis
To recover the Crysis encrypted files use one of the following decryptor tools:
- Kaspersky RakhniDecryptor tool
- Trend Micro Ransomware File Decryptor
- ESET decryption tool for Crysis ransomware
DMALocker & DMALocker2
DMALocker & DMALocker2 doesn’t changes the filenames and identifies itself as DMA Locker.
How to decrypt files encrypted DMALocker & DMALocker2.
To recover the files encrypted by DMALocker, use one of the following decryptor tools:
- DMALocker with ID “DMALOCK 41:55:16:13:51:76:67:99” use this tool: Emsisoft Decrypter for DMALocker
- DMALocker2 with ID “DMALOCK 43:41:90:35:25:13:61:92”, use this tool: Emsisoft Decrypter for DMALocker2
DXXD
DXXD ransomware appends the DXXD extension to the end of the original extension of each encrypted file.
How to decrypt files encrypted by DXXD Ransomware.
To recover the DXXD encrypted files use this tool: Trend Micro Ransomware File Decryptor
Fabiansomware
Fabiansomware malware adds the following extension to the end of each encrypted file: .encrypted and creates the following ransom notes at your desktop *.How_To_Decrypt_Your_Files.txt. The ransom note instructing you to contact decryptioncompany@inbox.ru or “fwosar@mail.ru” or “fabianwosar@mail.ru
How to decrypt files encrypted by Fabiansomware
To recover the Fabiansomware encrypted files use this tool: Emsisoft Decrypter for Fabiansomware
FenixLocker
FenixLocker malware adds the following extension to the end of each encrypted file: .centrumfr@india.com and creates the following ransom notes at your desktop “CryptoLocker.txt” or “Help to decrypt.txt”, instructing you to contact centrumfr@india.com.
How to decrypt files encrypted by FenixLocker
To recover the FenixLocker encrypted files use this tool: Emsisoft Decrypter for FenixLocker
Globe
Globe malware adds one of the following extensions at the end of each infected file: .purge, .globe, .okean.
How to decrypt files encrypted by Globe.
To recover the Globe encrypted files use one of the following tools:
- Emsisoft Decrypter for Globe
- Trend Micro Ransomware File Decryptor
Globe2
Globe2 ransomware adds one of the following extensions at the end of each infected file: .raid10, .blt, .globe, .encrypted, .[mia.kokers@aol.com
How to decrypt files encrypted by Globe2
To recover the Globe2 encrypted files use one of the following tools:
- Emsisoft Decrypter for Globe2
- Trend Micro Ransomware File Decryptor
Gomasom
Gomasom malware adds an email address (to contact) at the original filename and the extension .crypt at the end of each infected file.
How to decrypt files encrypted by Gomasom
To recover the Gomasom encrypted files use this tool: Emsisoft Decrypter for Gomasom
Harasom
Harasom malware locks Windows and prevent access to files and application until you pay the ransom. Also adds the extension .HTML to every infected file.
How to decrypt files encrypted by Harasom
To recover Harasom encrypted files use this tool: Emsisoft Decrypter for Harasom
HydraCrypt
HydraCrypt malware adds the following extension to the end of each encrypted file: .hydracrypt
How to decrypt files encrypted by HydraCrypt
To recover the HydraCrypt encrypted files use this tool: Emsisoft Decrypter for HydraCrypt
Jigsaw
Jigsaw ransomware adds one of the following extensiosn to the end of each encrypted file: .FUN, .KKK, .GWS, .BTC
How to decrypt files encrypted by Jigsaw
To recover the Jigsaw encrypted files use this tool:
- Trend Micro Ransomware File Decryptor
- Jigsaw Decrypter from BleepingComputer
KeyBTC
KeyBTC malware adds the extension .keybtc@inbox_com at the end of each infected file.
How to decrypt files encrypted by KeyBTC
To recover the KeyBTC encrypted files use this tool: Emsisoft Decrypter for KeyBTC
LECHIFFRE
LECHIFFRE malware adds the following extensions at the end of each infected file: .LeChiffre
How to decrypt files encrypted by LECHIFFRE.
To recover LECHIFFRE encrypted files use one of the following decrypter tolls:
- Emsisoft Decrypter for LeChiffre
- Trend Micro Ransomware File Decryptor
Legion (Democry)
Legion malware (also known as “Democry”) adds the following extensions at the end of each infected file: ._date-time_$address@domain$.777 OR ._date-time_$address@domain$.legion
e.g. ._23-06-2016-20-27-23_$f_tactics@aol.com$.legion OR .$centurion_legion@aol.com$.cbf
How to decrypt files encrypted by Legion/Democry.
To recover Legion encrypted files use one of the following tools:
- Kaspersky RakhniDecryptor tool
- AVG’s Legion Decryptor Tool
Lobzik
The Lobzik malware adds the following extensions at the end of each infected file: .fun, .gws, .btc, .AFD, .porno, .pornoransom, .epic, .encrypted, .J, .payransom, .paybtcs, .paymds, .paymrss, .paymrts, .paymst, .paymts, .payrms
How to decrypt files encrypted by Lobzik.
To recover Lobzik encrypted files use this tool: Kaspersky RakhniDecryptor tool
LockLock
LockLock malware adds the following extensions at the end of each infected file: .locklock and creates a ransom notes named READ_ME.TXT that asks the victim to contact the email address locklockrs@aol.com, or the Skype address “locklockrs“
How to decrypt files encrypted by LockLock.
To recover LockLock encrypted files see here: LockLock Ransomware (.locklock) Help & Support
Locky & AutoLocky
Locky malware changes the original filename and adds the extension .locky at the end of each encrypted file.
Autolocky is another variant of Locky virus, which doesn’t change the original filename but adds the extension .locky at the end of each encrypted file
How to decrypt files encrypted by Locky or AutoLocky.
Unfortunately at this time there is no way to recover files encrypted by Locky vurus (The original filename is changed). If you are lucky and the original filename is still unchanged (Infected from AutoLocky) then use one of the following tools to recover your files:
- Emsisoft Decrypter for AutoLocky
- Trend Micro Ransomware File Decryptor
Nemucod
Nemucod adds the following extensions at the end of each infected file: .crypted
How to decrypt files encrypted by Nemucod
To recover Nemucod encrypted files use one of the following decryptor tools:
- Emsisoft Decrypter for Nemucod
- Trend Micro Ransomware File Decryptor
NoobCrypt
NoobCrypt changes the original and uses the same encryption key for every victim.
How to decrypt files encrypted by NoobCrypt virus.
Thanks to Jakub Kroustek, a reverse engineer and malware analyst at AVG Technologies, who has posted the decryption keys for NoobCrypt in Twitter. Source and instructions: Decrypting NoobCrypt.
Operation Global III
Operation Global III (OF3) malware, encrypts user files and then displays a lock demanding for a ransom. After the encryption all file extensions are changed to .EXE and the OG3 virus tries to infect all other computers on the network.
How to decrypt files encrypted by Operation Global III (OG3) virus.
To recover OG3 encrypted files use this tool: OG3 Patcher
OzozaLocker
OzozaLocker malware, encrypts user files, adds the extension .locked at the end of each infected file and creates the following ransom notes: HOW TO DECRYPT YOU FILES.txt on the desktop.
How to decrypt files encrypted by OzozaLocker.
To recover OzozaLocker encrypted files use this decrypter tool: Emsisoft Decrypter for OzozaLocker
Petya
Petya malware denies access to the full system by attacking low-level structures on the disk. In fact overwrites the MBR (Master Boot Record) of your PC and leaves it unbootable.
How to decrypt files encrypted by Petya virus.
To recover Petya encrypted files follow the instructions on this page: Petya decrypt tool
PClock
PClock ransomware tries to pass as “CryptoLocker” and after infecting the system stores a list of all encrypted files inside “%UserProfileenc_files.txt”. file.
How to decrypt files encrypted by PClock
To recover PClock encrypted files use this tool: Emsisoft Decrypter for PClock
Philadelphia
The Philadelphia ransomware encrypts the filename and adds the extension .locked at the end of each infected file.
How to decrypt files encrypted by Philadelphia
To recover Philadelphia encrypted files use this tool: Emsisoft Decrypter for Philadelphia
Princess Locker
The Princess Locker encrypts files and adds a random extension at the end of each infected file.
How to decrypt files encrypted by Princess Locker
A decryptor tool, to recover Princess Locker encrypted files can be found here: Decryptor Available for Princess Locker Ransomware
Rakhni & Others
Trojan-Ransom.Win32.Rakhni, Trojan-Ransom.Win32.Agent.iih, Trojan-Ransom.Win32.Aura, Trojan-Ransom.Win32.Autoit, Trojan-Ransom.AndroidOS.Pletor, Trojan-Ransom.Win32.Rotor, Trojan-Ransom.Win32.Lamer, Trojan-Ransom.MSIL.Lortok, Trojan-Ransom.Win32.Cryptokluchen, encypts user files and adds several extensions at the end of filenames after infection: .locked, .kraken, .darkness, .nochance, .oshit, .oplata@qq_com, .relock@qq_com, .crypto, .helpdecrypt@ukr.net, .pizda@qq_com, .dyatel@qq_com, ._crypt .nalog@qq_com, .chifrator@qq_com, .gruzin@qq_com, .troyancoder@qq_com, .encrypted, .cry, .AES256, .enc, .coderksu@gmail_com_id371, .coderksu@gmail_com_id372, .coderksu@gmail_com_id374, .coderksu@gmail_com_id375, .coderksu@gmail_com_id376, .coderksu@gmail_com_id392, .coderksu@gmail_com_id357, .coderksu@gmail_com_id356, .coderksu@gmail_com_id358, .coderksu@gmail_com_id359, .coderksu@gmail_com_id360, .coderksu@gmail_com_id20, .crypt@india.com.random_characters, .+<hb15
How to decrypt files encrypted by Rakhni and friends.
To recover Rakhni encrypted files use this tool: Kaspersky RakhniDecryptor tool
Rannoh
Trojan-Ransom.Win32.Rannoh, Trojan-Ransom.Win32.Fury, Trojan-Ransom.Win32.Crybola encrypt files and after infection, file names and extensions will be changed according to the template: locked-{Original Filename} .<four_random_letters>.
How to decrypt files encrypted by Rannoh / Fury / Crybola.
To recover Rannoh encrypted files use this tool: Kaspersky RannohDecryptor.
Radamant
The Radamant malware adds the following extensions at the end of each infected file: .rdm or .rrk
How to decrypt files encrypted by Radamant.
To recover Radamant encrypted files use the following tool: Emsisoft Decrypter for Radamant
Rector
Trojan-Ransom.Win32.Rector encrypts files with extensions .jpg, .doc, .pdf, .rar. An offers to unblock files comes in from a cybercriminal named “††KOPPEKTOP††”. He is offering to communicate with him using the following contacts: ICQ: 557973252 or 481095 &
EMAIL: v-martjanov@mail.ru
How to decrypt files encrypted by Rector
To decrypt Rector encrypted files use this tool: Kaspersky Rector Decryptor tool
Shade version 1 & version 2.
The Shade ransomware adds one the following extensions at the end of each infected file: .xtbl, .ytbl, .breaking_bad, .heisenberg
How to decrypt files encrypted by Shade version 1 & version 2.
To recover Shade encrypted files use one of the following tools:
- Kaspersky ShadeDecryptor tool
- Intel McAfee Shade Ransomware Decryption Tool
SZFLocker
The SZFLocker ransomware adds the following extensions at the end of each infected file .szf
How to decrypt files encrypted by SZFLocker.
To recover SZFLocker encrypted files use: AVG SZFLocker Decryptor Tool.
SNSLocker
The SNSLocker ransomware adds the following extensions at the end of each infected file: .RSNSLocked
How to decrypt files encrypted by SNSLocker
To recover SNSLocker encrypted files use Trend Micro Ransomware File Decryptor tool.
Stampado
The Stampado ransomware adds the following extensions at the end of each infected file: .locked
How to decrypt files encrypted by Stampado
To recover Stampado encrypted files use on the following decryptor tools:
- Emsisoft Decrypter for Stampado
- Trend Micro Ransomware File Decryptor tool.
TeslaCrypt V1.0
The TeslaCrypt V1 ransomware adds the following extension at the end of each infected file: .ecc
How to decrypt files encrypted by TeslaCrypt V1
To recover TeslaCrypt V1 encrypted files use on the following tools:
- Trend Micro TeslacryptDecryptor.
- Cisco Talos TeslaCrypt decryptor tool
TeslaCrypt V2.0
The TeslaCrypt V2 ransomware adds the following extensions at the end of each infected file: .ezz, .exx, .xyz, .zzz,. aaa, .abc, .ccc, & .vvv
How to decrypt files encrypted by TeslaCrypt V2
To recover TeslaCrypt V2 encrypted files use on the following tools:
- Trend Micro TeslacryptDecryptor.
- Cisco Talos TeslaCrypt decryptor tool
TeslaCrypt V3.0 (Bitman V3.0)
The TeslaCrypt Version 3 ransomware (also known as “Bitman Version 3”)adds the following extensions at the end of each infected file: .xxx, .ttt, .micro, .mp3
How to decrypt files encrypted by TeslaCrypt V3 / Bitman V3
To recover TeslaCrypt V3 encrypted files use one of the following tools:
- Kaspersky RakhniDecryptor tool
- Trend Micro Ransomware File Decryptor tool.
- Cisco Talos TeslaCrypt decryptor tool
TeslaCrypt V4.0 (Bitman V4.0)
The TeslaCrypt Version 4 (also known as “Bitman Version 4”) ransomware leaves the filename and the extension unchanged.
How to decrypt files encrypted by TeslaCrypt V4 / / Bitman V4
To recover TeslaCrypt V4 encrypted files use one of the following tools:
- Kaspersky RakhniDecryptor tool
- Trend Micro Ransomware File Decryptor tool.
- Cisco Talos TeslaCrypt decryptor tool
- AVG Decryptor TeslaCrypt3 Tool
UmbreCrypt
UmbreCrypt malware adds the following extension to the end of each encrypted file: .umbrecrypt
How to decrypt files encrypted by UmbreCrypt
To recover the UmbreCrypt encrypted files use this tool: Emsisoft Decrypter for UmbreCrypt
Wildfire
Wildfire malware adds the following extension to the end of each encrypted file: .wflx
How to decrypt files encrypted by Wildfire
To recover the Wildfire encrypted files use one of the following this decrypter tools:
1. Kaspersky WildfireDecryptor tool
2. Intel McAfee WildFire Ransomware Decryption Tool
XORBAT
XORBAT adds the following extensions at the end of each infected file: .crypted
How to decrypt files encrypted by XORBAT
To recover XORBAT encrypted files use one of the following tools:
- Emsisoft Decrypter for Xorist
- Trend Micro Ransomware File Decryptor
XORIST & VANDEV
XORIST adds the following extension at the end of each infected file: .xorist (or adds a random extension)
How to decrypt files encrypted by Xorist & Vandev
To recover XORIST encrypted files use one of the following tools:
- Kaspersky XoristDecryptor tool
- Trend Micro Ransomware File Decryptor
XRatTeam / TeamXRat
XRatTeam ransomware adds the following extension to the end of each encrypted file: .xratteamLucked
How to decrypt files encrypted by XRatTeam / TeamXRa
To recover the XRatTeam encrypted files use this decryptor tool: Trend Micro Ransomware File Decryptor
Zepto
Zepto ransomware change the original filename and adds the following extensions at the end of each infected file: .zepto.
How to decrypt files encrypted by .Zepto
Unfortunately at this time it’s not possible to recover Zepto encrypted files.