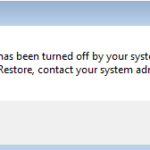
The “System Restore has been turned off by Administrator or Group Policy. To turn on System Restore, contact your domain administrator” error message, may displayed on a Windows 7, 8 or 10 based computer when the user tries to launch the system restore. The user is already logged in as Administrator and cannot enable the System Restore because the “Configure” button at System Protection settings is grayed out.
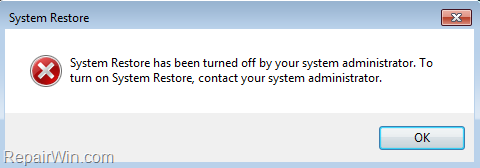
If the System Restore is disabled on your system and you cannot enable it, through the System Protections settings, then probably your computer is infected by a virus or other malware program.
This article contains instructions to fix the following problems in Windows 7, 8 or Windows 10 OS:
- System Restore has been turned off by Group Policy.
- System Restore has been turned off by your System Administrator.
- System Restore is Disabled.
- System Protection settings are greyed out.
How to FIX: System Restore has been turned off by your system administrator.
Notes about this guide: As I said above, the “System Restore has been turned off by your system administrator” error message, commonly is displayed after a virus infection. So, the steps 1-6 in this guide, will help you to clean your computer from virus or malware programs and the steps 5 & 6 shows how to re-enable System Restore on your system.
Step 1. Start your computer in Safe Mode with Networking.
First of all you have to boot your computer into safe mode to prevent malware programs from running. To do that:
- Windows 7, Vista & XP:
- Restart your computer and hit the “F8” key while your computer is starting up (before the appearance of Windows Logo).
- When “Advanced options” menu appears on your screen, navigate to “Safe Mode with Networking” option (using your keyboard arrow keys) option and hit Enter.
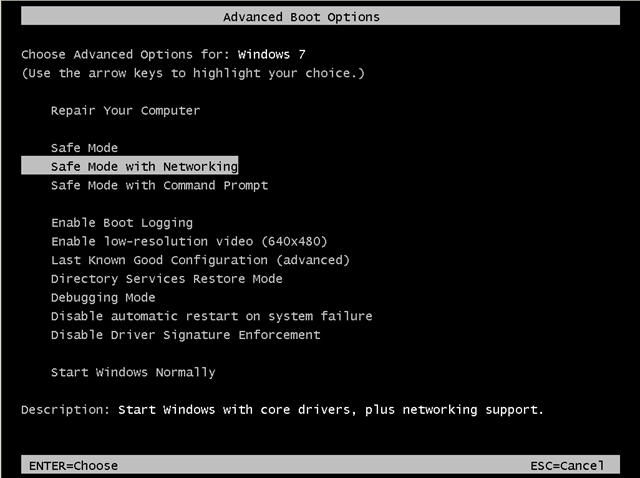
- Windows 10, 8.1/8 or 7:
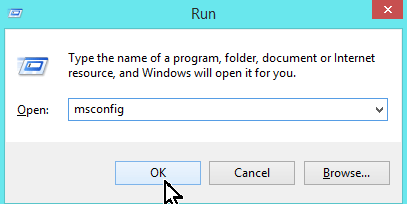
- Press “Windows” + “R” keys to open the RUN window.
- Type msconfig & press OK.
- Click the Boot tab.
- Select the Safe Boot & Network options & click OK.
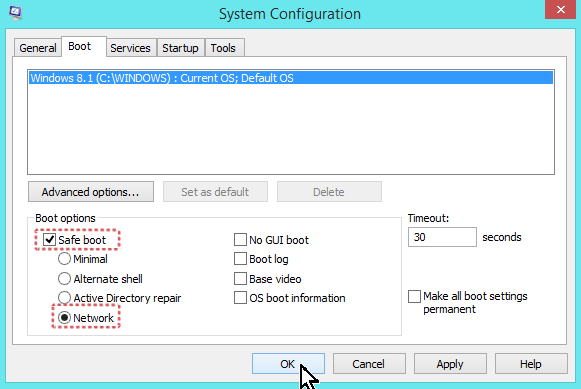
- Restart your computer.
Step 2. Remove Adware programs with AdwCleaner.
– AdwCleaner is a freeware utility that can clean your computer from adware programs.
1. Download AdwCleaner utility to your desktop.
2. Close all open programs and run AdwCleaner.exe.
3. At the main window, press the “Scan” button and wait until the scan is completed.

5. When the scan process is completed, press the Cleaning button to remove all adware programs detected.
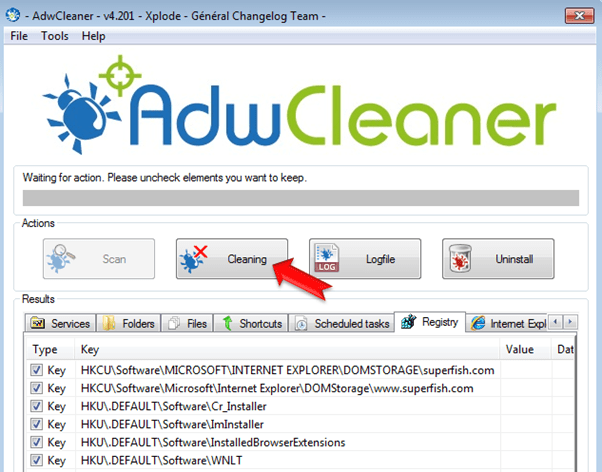
6. When prompted, press OK to restart your computer.
* Note: After restart, close the AdwCleaner report. The report contains the adware programs, registry keys and files that removed by AdwCleaner. If you want to examine its contents later, you can find the log file at “AdwCleaner” folder on the root drive. (e.g. “C:AdwCleanerAdwCleaner.txt)
Step 3: Remove Junkware files with JRT.
1. Download and save JRT-Junkware Removal Tool on your desktop.
2. Run JRT and press a key to start the scan.
3. Be patient until JRT scans and cleans your system from Junkware.
4. When the Junkware Removal Tool scan is completed, close the JRT log file and then reboot your computer again.
Step 4: Remove Malware programs with MalwareBytes Antimalware.
1. Download and install Malwarebytes 3.0 Free. *
* Note: Keep in mind that after the 14-day trial period, Malwarebytes reverts to a free version but without the full real-time protection.
2. Run Malwarebytes Anti-Malware and wait until the program updates its Malware Database.
3. Press the Scan Now button and then wait until the scan process is finished.
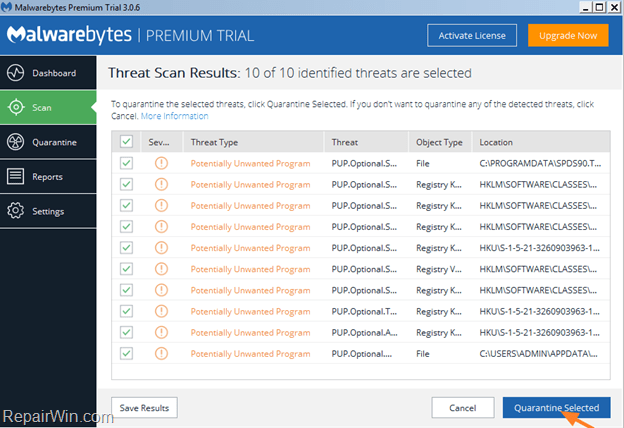
4. When the scan is completed select all items found and then press Quarantine All.
5. Restart your computer if needed and continue to the next step.
Step 5. Terminate and remove malicious processes with RKILL.
– RKill is a program that was developed at Bleepingcomputer.com that attempts to terminate known malware processes so that your normal security software can then run and clean your computer of infections. Additionally, the RKILL utility, examines the current status and configuration of some essential Windows components (Firewall, System Restore, etc.) and displays the scanning results in a helpful log file.
- Download and run RKILL.
- Be patient while RKILL terminates the malicious processes.
- When the RKILL completes its job, click OK.
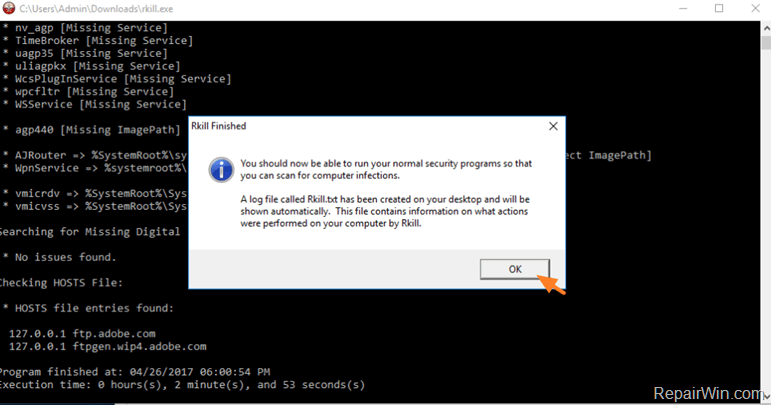
- Navigate to your desktop and open the RKILL.txt log file.
- In “Rkill.txt” log, look under the “Preforming miscellaneous checks” section, to find out in which registry key(s) the System Restore is disabled. *
e.g. As you see at the screenshot below, the System Restore is disabled at the the following registry key:
- HKLMSOFTWAREPoliciesMicrosoftWindows NTSystemRestore –> DisableSR = 1
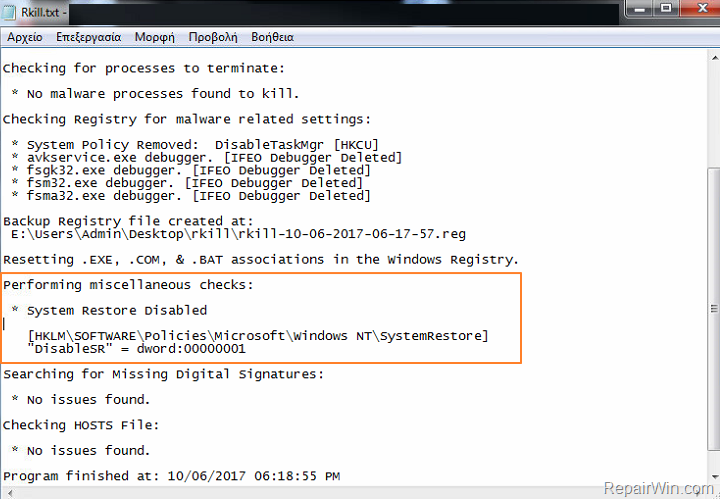
- Without closing the Rkill log file, proceed to the next step and Enable System Restore in registry.
Step 6. Enable System Restore using Registry.
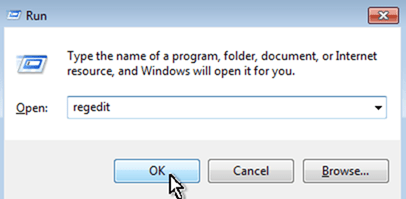
- Open open Registry Editor. To do that:
- Simultaneously press “Windows” + “R” keys to open the RUN window.
- In “RUN” window “Open” box, type: regedit
- Press Enter.
- Open open Registry Editor. To do that:
- From the left pane, navigate to the registry key mentioned in Rkill.txt log.
- HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindows NT
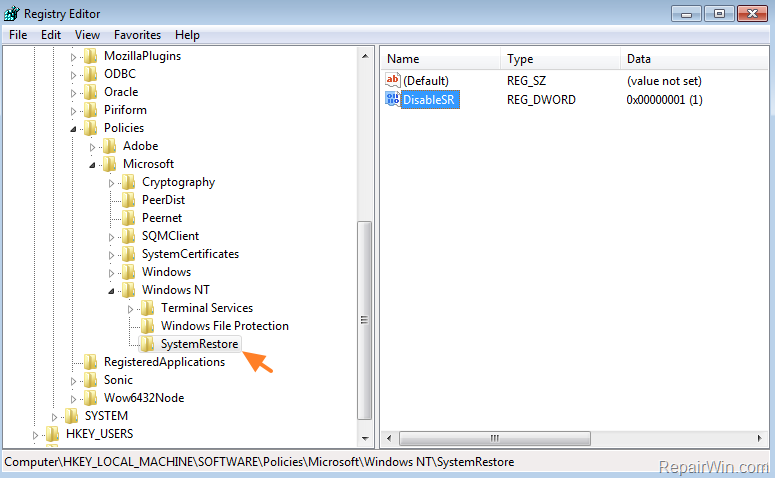
- At the right pane double click at DisableSR value and modify the value data from 1 to 0.
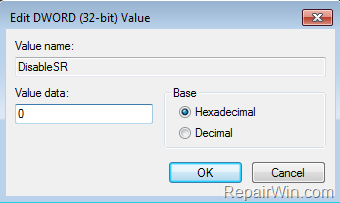
- Close Registry Editor* and restart your computer.
* If the Rkill.txt log, displays that the System Restore is disabled in more than one Registry Keys (locations), then proceed and apply the same steps (modify the “DisableSR” value to “0“) in all other registry keys that mentioned in RKILL.txt Log.
That’s all folks! Did it work for you?
Please leave a comment in the comment section below or even better: like and share this blog post in the social networks to help spread the word about this solution.