What is the “HELP_FILE” Cryptowall v4.0 virus?
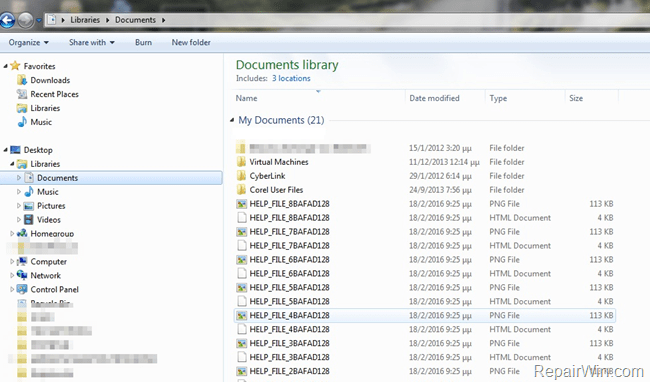
If you have discovered that all your files are missing or they have renamed with random characters, like “e9fgbb.ie0r“, “52lcvn.ifggh” “d3uhgfds.gre8v“, etc. and all your documents, pictures and desktop folders are full of HTML and PNG files with random filenames like “HELP_FILE_4BAACA128.PNG“, “HELP_FILE_4BAACA128.HTML“, etc. then, unfortunately, you have infected with the latest version of Cryptowall version 4.0 virus (Trojan-Ransom:Win32/Crowti-b).
The Cryptowall version 4.0 virus, is the latest version of Cryptowall family virus and upon infects your computer, encrypts all your important files with strong encryption and is impossible to decrypt them unless you pay the ransom. Compared to older version the new Cryptowall v4.0 ransomware virus, also encrypts the filenames, changes the name of your files to random characters and finally deletes the Volume Shadow Copies.
At the end of Cryptowall Version 4.0 infection, you receive a ransom demand message informing you that your files (documents, photos, videos, etc) are encrypted with a strong encryption and in order to decrypt them and get your encrypted files back, you have to pay the ransom by following the directions given inside the HELP_FILE .PNG and .HTML files.
HELP_FILE_Random_Characters.PNG & HELP_FILE_Random_Characters.HTML – Cryptowall V4.0 – information message (BEGIN) & Screenshots:
” Cannot you find the files you need? Is the content of the files that you have watched not readable?
It is normal because the files’ names, as well as the data in your files have been encrypted.
Congratulations!!! You have become a part of large community CryptoWall.
If you are reading this text that means that the software CryptoWall has removed from your computer…..
What is encryption?
Encryption is a reversible transformation of information in order to conceal it from unauthorized persons but providing at the same time access to it for authorized users. To become an authorized user and make the process truly reversible i.e. to be able to decrypt your files you need to have a special private key.
In addition to the private key you need the decryption software with which you can decrypt your files and return everything in its place.
I almost understood but what do I have to do?
The first thing you should do is to read the instructions to the end…..”

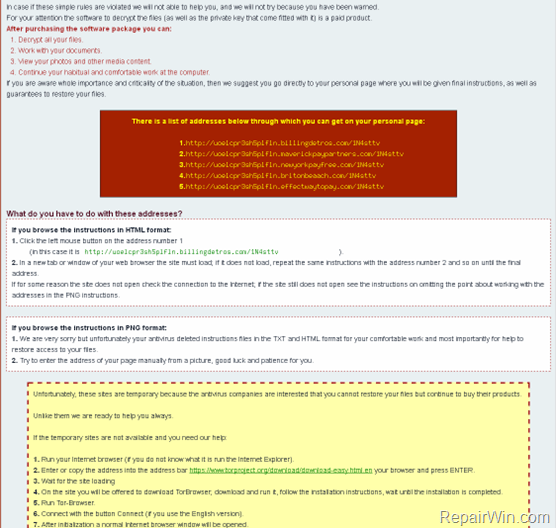
Inside the Cryptowall v4.0 ransomware HELP_FILE HTML & PNG messages you can find five (5) new payment sites, to visit with TOR browser in order to pay the ransom, and decrypt your files:
1. ht*p://uoelcp***.billingdetros.com/
2. ht*p://uoelcp***.maverickpaypartners.com/
3. ht*p://uoelcp***.newyorkpayfree.com/
4. ht**p://uoelcp***.britonbeaach.com/
5. ht*p://uoelcp***.effectwaytopay.com/
Many users (on the Internet) complained that their files remained encrypted even after they paid the ransom, so it’s your own decision (and risk) to pay (or not) the ransom and to support (or not) the criminals.
In this article you can find detailed instructions on how to remove the new HELP_FILE – Cryptowall v4.0 virus from your computer. Keep in mind that your files will be remain encrypted after the virus removal.
How to restore (decrypt) Cryptowall v4.0 encrypted files?
Unfortunately, there is not a way (like a free decryption tool or service) to decrypt Cryptowall v4.0 encrypted files. The only ways to get your files back are:
1. To copy your files back from a clean backup.
2. To restore the encrypted files by using Shadow copies, if you are too lucky and the virus doesn’t have deleted the Shadow Volume copies yet.
3. To pay the ransom and decrypt your files (I DON’T SUGGEST IT).
How to remove the Cryptowall v4.0 (Crowti-b) ransomware virus-trojan infection?
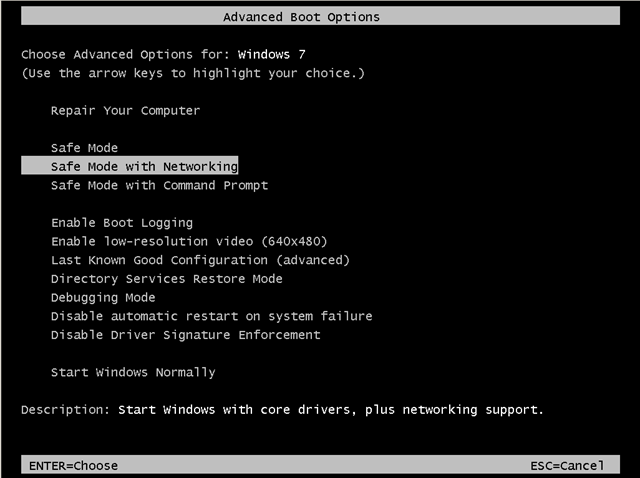
Step 1. Start your computer in Safe Mode with Networking.
First of all you have to boot your computer into safe mode to prevent Cryptowall virus from running. To do that:
- Windows 7, Vista & XP:
- Restart your computer and hit the “F8” key while your computer is starting up (before the appearance of Windows Logo).
- When “Advanced options” menu appears on your screen, navigate to “Safe Mode With Networking” option (using your keyboard arrow keys) option and hit Enter.
- Windows 8 & Windows 8.1:
- Press “Windows” + “R” keys to open the RUN window.
- Type msconfig & press OK.

- Click the Boot tab.
- Select the Safe Boot & Network options & click OK.

- Restart your computer.
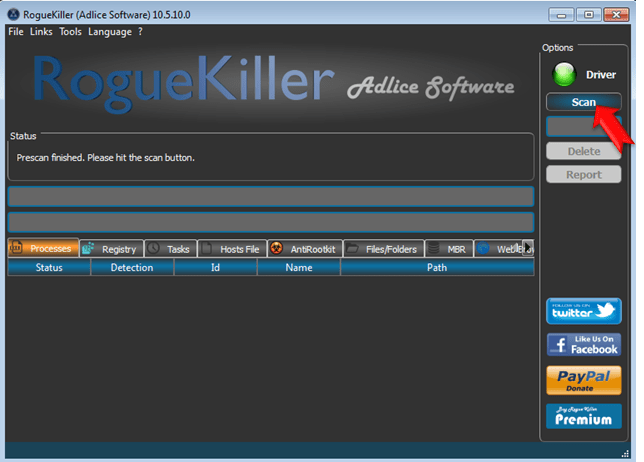
Step 2. Terminate and remove Cryptowall infection with RogueKiller.
– RogueKiller is an freeware anti-malware program, able to detect and remove generic malwares and some advanced threats such as rootkits, rogues, worms, etc.
- Download and run RogueKiller. (Download a compatible version for your system 32bit or 64bit)
- Allow the Pre-Scan to complete and then press the Scan button.
- Be patient until Rogue Killer scans your system.
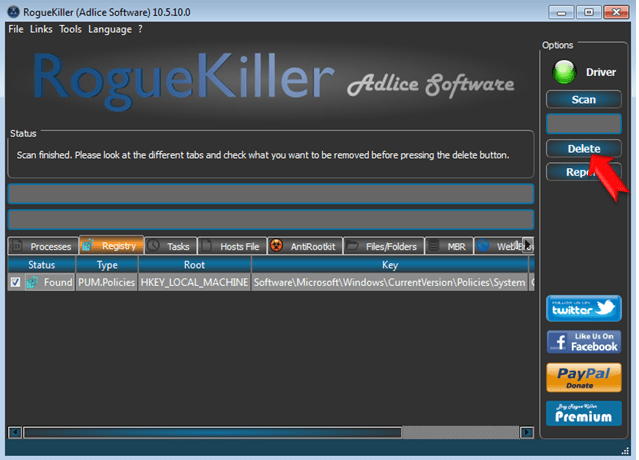
- When the scan is completed, select all items found at Registry & Web Browsers tabs.
- Press the “Delete” button to remove items found.
Step 3: Remove Cryptowall version 4.0 malware infection with MalwareBytes Anti-Malware.
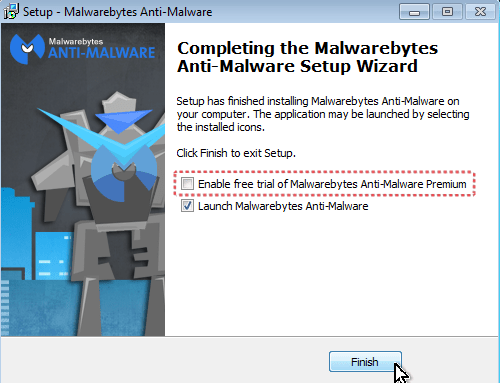
- Download and install Malwarebytes Anti-Malware Free. *
* Beware: at the last screen of installation, uncheck the box next to “Enable free Trial of Malwarebytes Anti-Malware PRO” in order to use the free version of this GREAT software.
- Run Malwarebytes Anti-Malware.
- Update the Database.
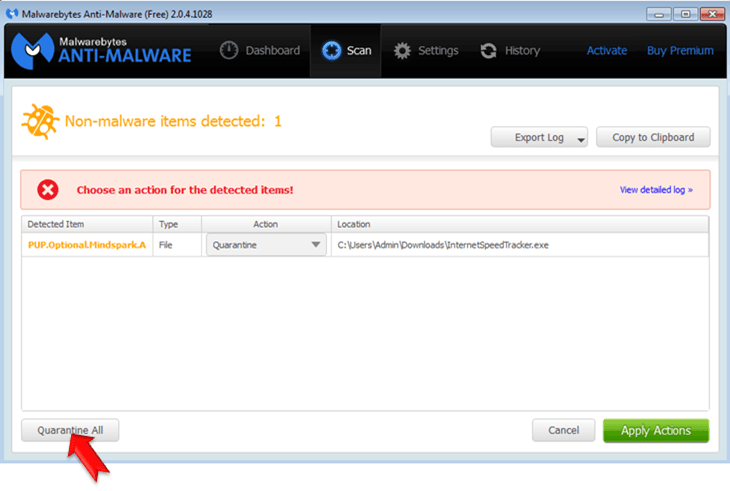
- Press the Scan Now button and then wait until the scan process is finished.

- When the scan is completed select all items found and then press Quarantine All.
- Restart your computer if needed and you ‘re done.

Step 4. Scan your system with Eset Online Scanner.
1. Run Eset Online Scanner. If you use a browser other than Internet Explorer click to download (& run) the Eset Smart Installer. (esetsmartinstaller_enu)

2. Accept the license terms and click Start.

3. Wait from ESET Online Scanner to download required components and then:
a. Check the Enable detection of potentially unwanted applications.
b. Check all the options under “advanced settings”. (see screenshot below).
c. Press the Start button to scan and remove viruses and malware programs from your computer.

4. Be patient until the ESET online scanner removes all threats found.
That’s all folks! Did it work for you?
Please leave a comment in the comment section below or even better: like and share this blog post in the social networks to help spread the word about these really annoying crap Windows infections.


